Security Policy Manager
Secure critical content across multiple repositories with need-to-know security access, without affecting productivity or performance.
Secure and protect sensitive information
iManage Security Policy Manager allows organizations to enforce need-to-know security and information barriers at scale to meet the growing needs of client, regulatory, and company obligations without sacrificing user productivity and system performance — from an intuitive, role-based interface with anywhere, anytime access. Our group security policy allows administrators to set access based on profile hierarchy.
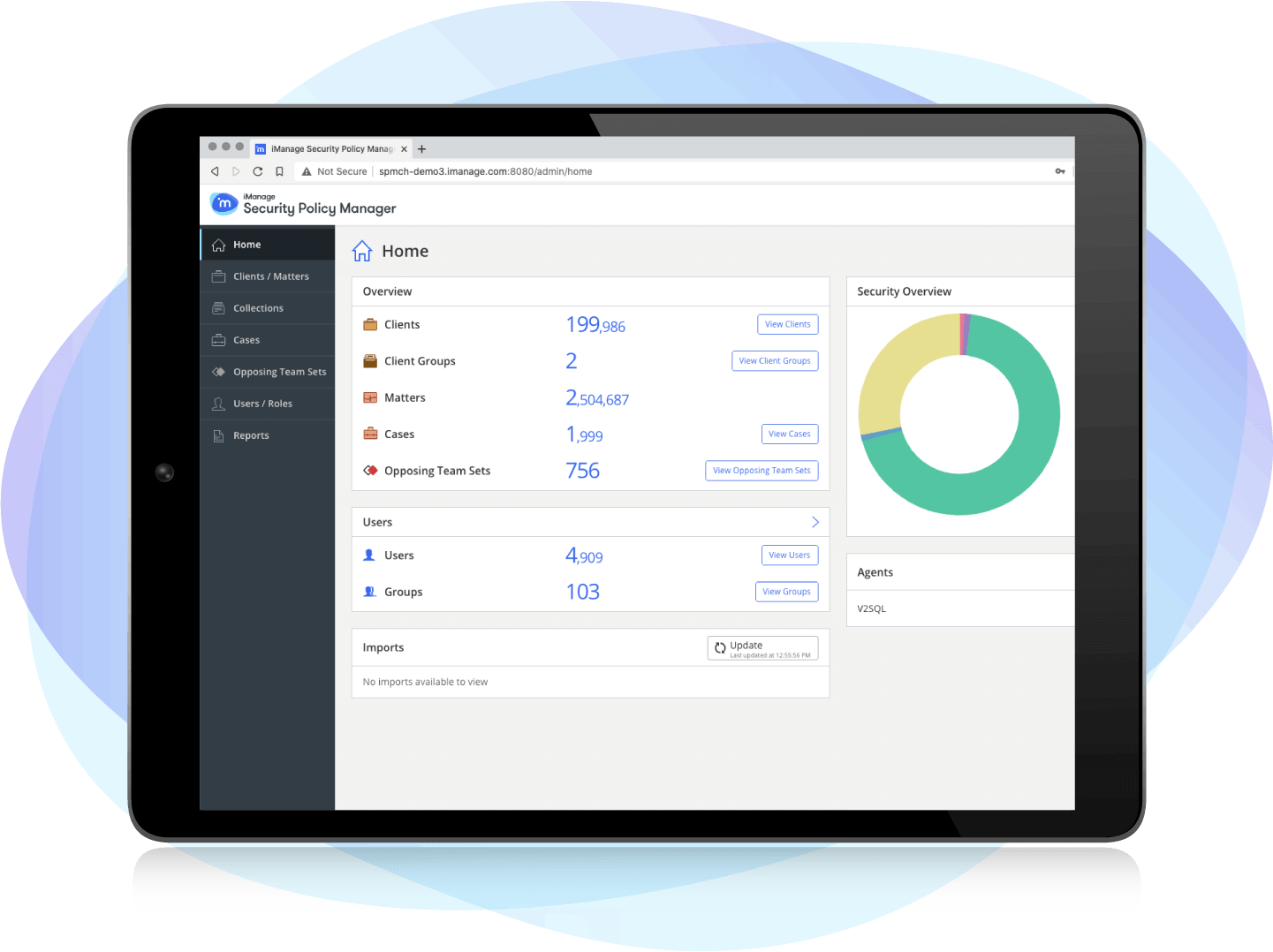
Using Security Policy Manager
Learn more in this set of videos and see how iManage Security Policy Manager can help you
Security Policy Manager Benefits

Seamless platform integration
Single vendor solution that delivers comprehensive security policy management to meet increasing demands:
- Establish, adjust, and remove security policies without access control cascades, document re-files, or content re-indexing.
- Search large workspaces without impacting performance.

Adaptable access requests
Granular and flexible access controls to suit any request:
- Configurable to follow Outside Counsel Guidelines (OCG) or company mandates.
- Access after reviewing by authorized users.
- Break-Glass – instant access granted for a limited time.

Comprehensive security framework
Deploy “need-to-know” policies to secure information by department, function, project, or matter
- Delegation removes central IT and service desk bottlenecks.
- Self-maintaining rules help automate processes.
- Collections allow grouping using descriptive metadata tags.

Powerful reporting drives compliance
Extensive auditing and reporting capability to satisfy the most stringent request
- Automatically generated for any given date range.
- Removes uncertainty with no back-door unaudited access to content.
- Market Abuse Regulation (MAR) compatible insider reports.

Safeguarding your sensitive information
A comprehensive, layered approach to security keeps sensitive documents and emails safe from external threat actors and internal misuse. Discover the many ways that iManage protects what matters to your business.
Security Policy Manager Key Features
-
Security and governance built into the fabric of the knowledge platform to protect all content.
-
Extensible REST API and agent framework broadens the reach of Security Policy Manager to support new systems.
-
Options allow assistants to follow timekeepers to enable automatic enforcement of access rights and exclusions.
-
Visual cues in iManage Work and Records Manager clients clearly indicate security policies, eliminating access ambiguity.
-
The end-user console allows knowledge workers an "at-a-glance" view of the highly sensitive projects they are authorized to work on.
-
Email policies defined in Security Policy Manager can be enforced by partner products.
Learn more
Discover how your organization can implement secure access controls with Security Policy Manager.
Maintaining confidentiality as part of your client intake process
How iManage helps risk and compliance professionals adhere to changing regulations and ethical guidelines while protecting brand reputation.